What is Cyber Threat Intelligence? An introductory guide

The cybersecurity landscape is constantly evolving, marked by the growth and unpredictability of threats.
Never before have hackers had the ability to design threats that are increasingly complex and targeted, capable of remaining hidden within corporate IT infrastructures.
Organizations must adapt their defense strategies to the fluid nature of cybercrime, employing tools that can detect signs of compromise and anomalies before they escalate into full-blown attacks.
This is where the technique of Cyber Threat Intelligence comes into play.
What is Cyber Threat Intelligence?
Cyber Threat Intelligence (CTI) is the process through which an organization collects, processes, analyzes, and uses information related to potential or existing threats.
Its goal is to anticipate, detect, and respond effectively to attacks through a proactive approach.
For an SME or a mid-sized company, adopting CTI means shifting from a reactive posture (“we only notice the attack when it’s underway”) to a more proactive one (“we know what can happen, who might attack us, and how to defend ourselves”).
In this sense, CTI is a strategic pillar of modern cybersecurity.
The difference between Threat Data and Threat Intelligence
Threat Data and Threat Intelligence are two fundamental factors in threat detection, but they represent two different concepts:
- Threat Data consists of raw threat-related data: for example, malicious IP addresses, file hashes, suspicious domains, or network logs. Without further context, they are merely “alerts” but do not explain the “who,” the “why,” or the “how”.
- Threat Intelligence is the result of analyzing, contextualizing, and enriching this data. It involves transforming raw data into useful knowledge, complete with context, priority, and actionable recommendations.
For example: knowing that a certain hash is associated with malware is not enough. Knowing that this malware is used by an APT (Advanced Persistent Threat) group operating in your sector, which has similar targets to yours, and that exploits an undetected vulnerability in your infrastructure—that is intelligence.
This transition is crucial to avoid being overwhelmed by low-priority alerts and to focus on what truly matters.
What are the 4 Types of Cyber Threat Intelligence?
In a practical context, the main types of CTI are primarily distinguished by their recipients, depth, level of detail, and time horizon. The 4 categories of Cyber Threat Intelligence are as follows:
Technical Intelligence
This is the most “micro” from a technical perspective. It includes detailed information on malware, exploits, vulnerabilities, signatures, hashes, and command-and-control domains. It is useful for SOC teams for immediate intervention.
Tactical Intelligence
This concerns Indicators of Compromise (IoCs), and the Tactics, Techniques, and Procedures (TTPs) of attackers. It aims to improve detection and response in the short term.
Operational Intelligence
This analyzes active campaigns, the attackers’ modus operandi, the vulnerabilities they are exploiting in the specific context of the organization or sector, and probable attack vectors.
Strategic Intelligence
This is aimed at decision-makers, management, and the board. It provides an overview of threats, long-term trends, business impact, global scenarios, and security investments.
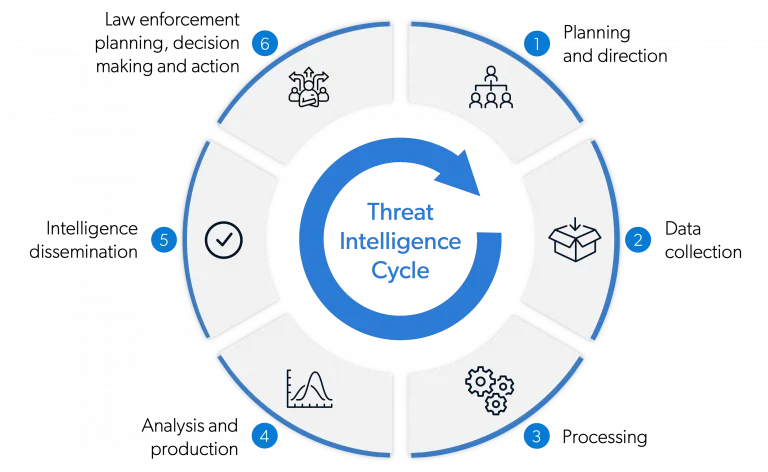
What are the 5 Stages of Cyber Threat Intelligence?
The management of CTI can be viewed as a cycle, a sequence of phases that leads from defining requirements to action and continuous improvement:
- Planning / Direction: defining what we want to understand: which assets are critical, which threats concern us, and which questions we need to answer.
- Collection: acquiring data from internal and external sources: logs, threat feeds, the dark web, OSINT, and known vulnerabilities.
- Processing: organizing and normalizing the data, filtering out noise, enriching it with context, and structuring the elements for analysis.
- Analysis: transforming the processed data into intelligence. This involves evaluating the “who,” “why,” and “how,” the implications for the organization, and defining recommendations.
- Dissemination / Use & Feedback: dstributing the intelligence to the appropriate stakeholders (SOC, management, IT team), implementing the suggested actions, and collecting feedback to refine the program.
What types of Threat Information exist?
Within CTI, the information collected and processed can be classified into several categories useful for protecting the company:
- Indicators of Compromise (IoCs): IP addresses, domains, file hashes, URLs, malware signatures, useful for technical detection.
- Attacker tactics, techniques, and procedures (TTPs): how they operate, which vulnerabilities they exploit, and which infrastructures they use.
- Attacker profiling: APT groups, cybercriminals, insider threats, their motivations, capabilities, and objectives.
- Vulnerabilities and exploits: which flaws are actively being exploited, and which business contexts are most at risk.
- Threat trends and scenarios: evolution of campaigns, most affected sectors, and emerging vectors (ransomware, supply-chain, IoT, Cloud).
- Business/Organizational context: which company assets are critical, what reputational or operational risk is being run, and which business processes are targets.
By integrating these types of information, CTI becomes a tool that connects the technical world to the business dimension.
It’s not just about “blocking a malicious IP,” but about understanding that “this threat could damage the continuity of our service X and the company image”.
The benefits of Cyber Threat Intelligence
Why invest in CTI? Here are some of the most significant advantages for SMEs and mid-to-large organizations:
- Threat Anticipation: by knowing the attackers’ techniques and preferred vectors, it is possible to prepare preventively, reducing reaction time.
- Better Risk prioritization: thanks to intelligence, resources can be focused on what truly matters (critical assets, probable attacks) instead of dispersing efforts.
- SOC operational efficiency: reduction of false positives, better alert triage, and more targeted interventions.
- Support for management decisions: by providing a strategic view of cyber risk, CTI helps CISOs/DPOs/Account Managers define budgets, processes, and investments.
- Integration and synergy with other security processes: Vulnerability management, incident response, and threat hunting all benefit from intelligence.
Greater Corporate Resilience: In the event of a real attack, an organization well-prepared with CTI can limit the impact, recover more quickly, and reduce reputational and operational damage.
Cyber Threat Intelligence vs. Threat Hunting
It is helpful to clarify how CTI differs from and integrates with an often-confused activity: Threat Hunting.
Cyber Threat Intelligence primarily deals with the collection, analysis, and dissemination of information about external or incoming threats: “What’s out there? Who might attack us? What vectors do they use?”
Threat Hunting, on the other hand, is a proactive activity within the organization. Analysts actively search for signs of compromise, anomalies, and suspicious behaviors that might evade automated tools.
CTI provides the “map” (who, what, where, how), and threat hunting does the “field research” (checking if someone is already inside, hidden).
The two work together: good intelligence feeds threat hunting with context, TTPs, and known situations; threat hunting returns internal data that enriches the intelligence.
Cyber Threat Intelligence Feeds by SGBox
Within the SGBox SIEM module, a distinctive component lies in the Threat Intelligence Feeds.
These feeds are curated data and analysis streams, specifically geared toward the needs of SMEs and the Italian markets, which include:
- Timely indications on IoCs, TTPs, and attacker groups relevant to the client company’s sector.
- Contextualization in the regulatory sphere (e.g., GDPR, NIS2), useful for compliance with regulations.
- Strategic reports that support management in viewing cyber risk and planning investments.
- Integration with SOC/MSPs managed by SGBox, to translate intelligence into operational action.
- Usable formats (reports, alerts, dashboards) designed to facilitate understanding by non-specialist IT Managers and Account Managers.
Thanks to this solution, SGBox allows small and medium-sized enterprises to proactively access CTI that would otherwise be difficult to implement internally, due to both cost and expertise.

