The most widespread cyberattacks in 2025

Today’s digital landscape, marked by the proliferation of digital devices and new technologies, is seeing a rise in cyber threats that can compromise data integrity and operational security in organizations.
But which are the most common attacks? And how can you protect yourself?
We discuss this in the following article, analyzing the most prevalent attacks and emerging trends across key industries, and showing how SGBox can provide the tools needed to enhance organizational cybersecurity.
Cyberattacks in 2025
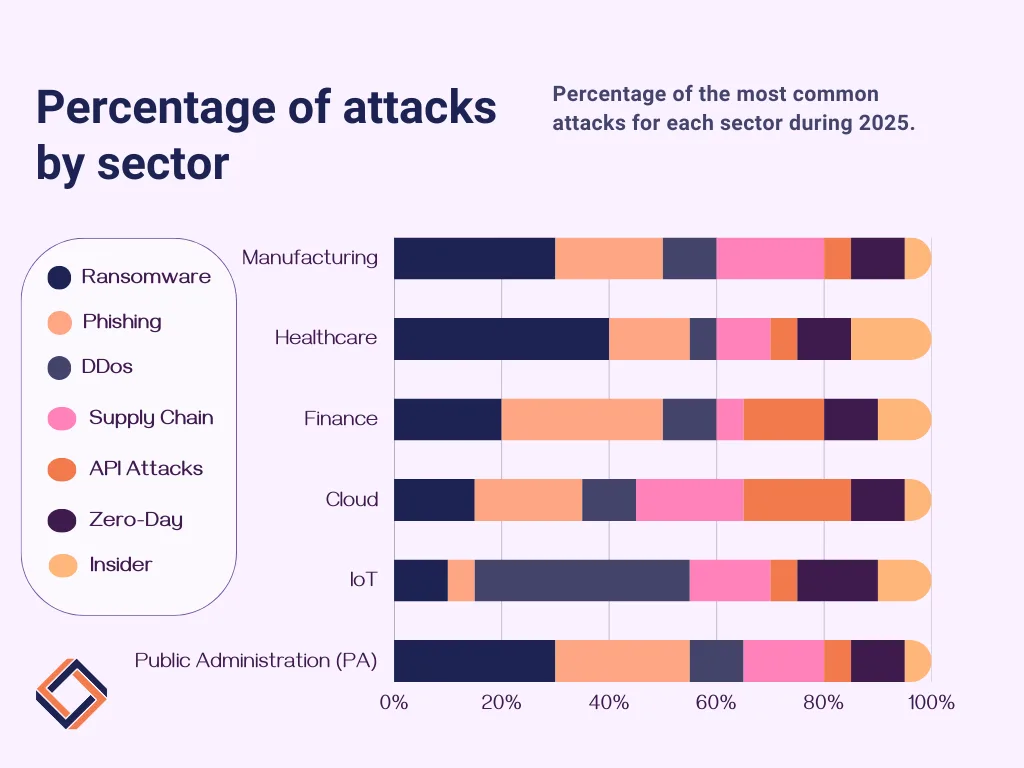
In 2025, the manufacturing, healthcare, and financial sectors, along with cloud and IoT technologies, are facing a proliferation of sophisticated cyberattacks.
The main threats confirm and intensify known trends: ransomware (often delivered as a service – Ransomware-as-a-Service), advanced phishing campaigns (sometimes AI-driven), software supply chain compromises, DDoS attacks (including ransom DDoS – RDoS), and zero-day vulnerabilities.
New technologies (generative AI, cloud microservices, IoT devices) and geopolitical tensions (e.g., international conflicts) have driven criminals to innovate: API attacks are on the rise, AI is being used to craft personalized phishing, and enhanced IoT botnets (Mirai/R2-D2) are powering mega DDoS attacks.
At the same time, there is a growing number of malware-free attacks, targeted social engineering, and cloud credential compromises.
From a regulatory perspective, directives like NIS2 in the EU, along with emerging laws on AI and healthcare data, have expanded the risk landscape for SMEs.
Summary of Key 2025 Attacks by Sector/Technology (Source: ENISA Europe):

Main trends in Cyberattacks
- Ransomware on the rise: it remains the number one threat across all sectors. Victims range from major manufacturers to hospital networks; in 2024, 65% of industrial companies suffered ransomware attacks.
- The ransomware-as-a-Service model continues to spread: new groups like RansomHub (active since 2024) allow even less skilled criminals to launch attacks. On the other hand, international law enforcement has struck major gangs, but the impact is limited due to the rapid emergence of replacements.
- Malware-free and AI-driven attacks: advanced techniques are increasingly used, leaving no traditional payload. Cyber criminals leverage generative AI to create highly convincing phishing and custom exploits.
- Supply Chain and third parties: attacks on the software and hardware supply chain are increasing. Vulnerable firmware and open-source libraries are preferred targets: in 2024, a backdoor was found in an open-source project, discovered only due to unusual CPU spikes. Organizations, including SMEs, must now treat third-party providers and software vendors as potential attack vectors.
- Geopolitics and hacktivism: the Russia-Ukraine war and other conflicts have driven waves of DDoS attacks and disinformation campaigns. In finance, geopolitical events triggered DDoS surges (e.g., 58% of attacks targeted European banks). Manufacturing, with global supply chains, is also exposed to political tensions: state actors seek industrial data or aim to disrupt adversaries’ critical production.
- Regulations and compliance: in Europe, new directives like NIS2 and DORA mandate cybersecurity measures in many sectors (including manufacturing and finance SMEs). Additionally, the EU’s AI Act imposes strict rules on AI use (e.g., in factories or financial services).
In healthcare, stricter data protection requirements (e.g., Health Information laws) are pushing SMEs to enhance internal controls. These regulations increase penalties in the event of an incident and raise the minimum standards for defense.
How SGBox protects organizations from Cyberattacks
Detects early signs of an attack
The SGBox Platform analyzes everything happening in IT systems in real time (logins, suspicious activity, intrusion attempts) and immediately alerts if something is wrong.
Aggregates and correlates data across technologies
Whether it’s an industrial machine, a healthcare app, or a financial system, SGBox connects the data, providing a comprehensive and up-to-date risk overview.
Responds automatically to limit impact
When it detects a real threat, SGBox can automatically trigger actions such as blocking suspicious access, isolating a device, or alerting IT staff.
Identifies unauthorized or unusual activity
It can detect when a user, even with valid credentials, does something unusual or risky—like accessing sensitive data at odd times or from unexpected locations.
Monitors Cloud services and secures digital identities
As more data moves online (e.g., Microsoft 365, SPID, digital healthcare services), SGBox checks for misconfigurations, unauthorized access, or credential theft risks.
Constantly monitors connected devices, even hidden ones
From medical tools to factory equipment and smart office devices, SGBox detects anomalies even in the hardest-to-monitor endpoints.
Supports regulatory compliance
SGBox generates automated reports and dashboards to help companies demonstrate compliance with increasingly strict regulations such as NIS2, GDPR and more.
Streamlines SOC team workflows
With SGBox, SOC teams have a powerful tool for monitoring, analyzing, and responding to critical events—all in one platform.
Thanks to its SIEM (Security Information & Event Management) functionality, all security information is centralized, offering clear and immediate insights into the most critical threats the SOC can act on without delay.
The SG-SOC Service by CyberTrust 365
Building on the SGBox SIEM & SOAR Platform, the SG-SOC managed service provides full cybersecurity activity management and 24/7 monitoring.
Here’s how CyberTrust 365’s SG-SOC as a Service helps organizations in manufacturing, healthcare, finance, cloud, IoT, and public administration address identified threats:
24/7/365 monitoring by a dedicated team
An external SOC department that’s always on, constantly monitoring your infrastructure and responding immediately to anomalies.
Early warning advisory
Continuous gathering and classification of threat intelligence sources to promptly alert you to emerging threats before they cause damage.
Automated Incident Response
Thanks to SOAR integration, SG-SOC can execute automated playbooks (system isolation, IP/domain blocking, IT team alerts) to quickly contain attacks like ransomware or credential compromises.
Centralized Log analysis (SIEM)
All events from networks, endpoints, cloud, and IoT feed into a single platform that correlates them in real time, allowing you to detect advanced phishing or malicious intent early.
Proactive Vulnerability Management
Regular scans and detailed reports on weaknesses (including OT/IoT devices and legacy software) to plan patches and reduce the attack surface.
Exposed surface mapping and protection (EASM)
Automated checks of external assets, cloud services, and public resources (e.g., SPID portals, PagoPA) to find insecure configurations or Dark Web leaks.
Advanced MITRE ATT&CK detection
Analysis of indicators of compromise and attacker TTPs (Tactics, Techniques & Procedures) to pre-empt APTs, supply chain attacks, and DDoS campaigns.
Incident handling & forensic analysis
In case of a breach, SG-SOC immediately initiates forensic investigations to trace the attack chain, eliminate residual threats, and support compliance processes.
Compliance Support
Ready-to-use reports and dashboards to help meet regulatory requirements (e.g., NIS2, GDPR, AdS), simplify audits, and reduce the risk of fines.
Scalability and Plug-and-Play Integration
SG-SOC adapts to the needs of both SMEs and large enterprises, requiring no extra infrastructure or in-house expertise. It integrates with existing IT tools, cutting down costs and implementation time.



