What is SIEM? Features and benefits

What is SIEM: definition
The SIEM (Security Information & Event Management) is one of the most effective solutions for managing vulnerabilities in companies IT infrastructures.
This solution allows real-time monitoring of the security status of the IT infrastructure and proactive intervention in case of an attack.
This is achieved through the collection, correlation and in-depth analysis of information gathered from security events.
In the current era marked by the rise of cyber attacks, investing in a SIEM solution means having an indispensable ally to enhance corporate security.
In this article, we delve into what this technology entails, its developments, and the benefits of its usage.
SIEM stands for Security Information & Event Management. It combines SIM (Security Information Management) and SEM (Security Event Management). In more detail:
SIM automates the collection and orchestration of logs (though not in real-time). Data is collected and sent to a centralized server using software agents installed on various monitored system devices.
Long-term storage and data analysis enable the generation of customized reports.
SEM is a real-time software solution that monitors and manages events within the network and various security systems.
It provides correlation and aggregation of events through a centralized console interface dedicated to monitoring, reporting, and automatically responding to specific events.
How does SIEM work?
The SIEM operation process starts with the collection and advanced management of logs from different IT devices.
Ultimately, a SIEM solution offers a centralized view with additional insights, combining context information about your users, assets and more.
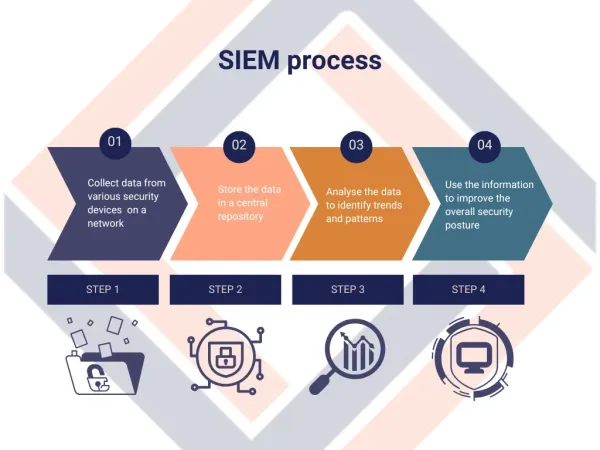
Data sources can include:
- Network devices: routers, switches, bridges, wireless access points, modems, line drivers, hubs
- Servers: web, proxy, mail, FTP.
- Security devices: Intrusion prevention systems (IPS), firewalls, antivirus software, content filter devices, intrusion detection systems (IDS) and more.
- Applications: any software used on any of the above devices.
- Cloud and SaaS solutions: software and services not hosted on-premises.
The data is then analyzed and correlated to detect anomalies, critical issues, and risks, activating preventive or corrective security procedures.
Another crucial function is reporting. Detailed reports enable thorough audits and analyses of threat entities, allowing easy identification of weaknesses in the IT infrastructure.
What is Correlation Rule in SIEM?
The correlation rule of events is a fundamental moment of a SIEM solution. Using advanced analytics tools to identify and understand complex data models, event correlation rule provides insights that can help you quickly identify and mitigate potential business security threats.
SIEM improves the average detection time (MTTD) and average response time (MTTR) of IT security teams, lightening manual workflows associated with in-depth security event analysis.
SIEM and Data Privacy
This technology is a valuable ally for complying with data processing regulations.
Collected data is encrypted and timestamped to preserve and make it immutable over time. Data retention policy is a fundamental aspect that highlights the transparency and usability of SIEM technology for businesses and organizations operating in the public sector.
Traditional SIEM vs Next Generation SIEM
The differences between a traditional SIEM and a Next Generation SIEM are significant and reflect the evolution of cybersecurity technologies.
- Architecture and Functionality: traditional SIEMs are designed to centrally collect and manage information and security events from different devices and systems, such as workstations, firewalls, and applications.
These systems have been developed to reduce false positives generated by intrusion detection systems (NIDS) and to provide a consolidated view of security events.
Traditional tools are complex to install and use, and were initially used only by larger organizations.
On the other hand, Next Generation SIEM has been designed to integrate technologies from SOAR (Security Orchestration, Automation, and Response), UBA (User Behavior Analytics), Threat Intelligence and Network Vulnerability Scanner.
This approach allows you to manage security threats more efficiently by automating and orchestrating threat responses.
- Analysis and Correlation: traditional SIEMs focus on collecting, correlating and analyzing data from different devices and systems to identify security threats.
However, Next Generation SIEMs use threat models to determine threats, rather than simply collect and analyze data. This approach allows you to detect more complex threats and intervene more quickly and accurately.
- Integration and Scalability: Next Generation SIEM are designed to be more scalable and integrated with other security technologies, such as firewalls and intrusion detection systems.
This allows you to collect and analyze data from a wide range of sources, including network and endpoint data, to provide a more comprehensive view of threats.
- Adaptability and Artificial Intelligence: Next Generation SIEM is designed to adapt to the specific needs of businesses and to use artificial intelligence to improve threat detection capabilities. This allows you to detect more complex threats and intervene more quickly and accurately.
The role of UBA in SIEM
One of the key functionality in SIEM tool is the UBA (User Behavior Analytics), that is used to discover internal and external threats.
The role of UBA within is the following:
- Creating a behavioral baseline for any user and highlight deviations from normal behavior.
- Monitoring malicious behavior and preventatively addressing security issues.
This function play a critical role in the SIEM activity, because it can show patterns of behavior within the organization IT network, offering advanced contextual security information.
SGBox’s Next Generation SIEM
SGBox’s SIEM offers advanced centralized data collection and security data processing capabilities.
It is a Next Generation technology that combines traditional SIEM capabilities with SOAR (Security Orchestration Automation and Response), UBA (User Behavior Analytics), Threat Intelligence, and Network Vulnerability Scanner technologies.
A key factor is the ability to set correlation rules that, thanks to machine learning processes, automatically activate in the event of an anomaly or a specific type of attack.
This translates into the ability to respond quickly and precisely to attacks, incidents, or malfunctions through a Detection activity that anticipates the occurrence of attacks and determines the most effective way to intervene.
The analysis and reporting of security events are also preparatory for the Security Operation Center (SOC) team.
SIEM vs SOAR: what are the differences?
The main differences between SIEM and SOAR lie in the capabilities and approach to managing cybersecurity.
SIEM (Security Information and Event Management): focuses on collecting, correlating and analyzing data from different devices and systems to detect security threats. It offers a consolidated view of security events.
SOAR (Security Orchestration, Automation, and Response): goes beyond simple data collection and analysis, integrating automation and orchestration of threat responses. This approach allows you to manage security threats more efficiently.
The capabilities of SIEM and SOAR are integrated within the SGBox platform, while presenting substantial differences.
These two modules work in synergy, exchanging safety information and optimizing the functionality of the other SGBox modules.
SIEM best practices
Getting started with SIEM (Security Information & Event Management) requires careful planning, execution, and ongoing review to ensure that the system meets the organization’s security and compliance needs.
Here are the best practices to follow:
Define clear objectives
- Identify Your Specific Requirements:
- Determine your organization’s specific security and compliance requirements.
- Identify key security problems or concerns and how you anticipate your SIEM solution can help in these areas.
- Rank your priorities to guide the implementation process.
Establish a team
- Build a Dedicated Response Team:
- Assemble a well-trained response team that can detect, analyze, and respond to security issues.
- Ensure that the team is equipped to handle security incidents promptly and effectively.
Conduct test runs
- Conduct Test Runs on Use Cases:
- Pilot the SIEM system on a small, representative subset of the organization’s technology and policies.
- This step helps uncover and address any weaknesses or gaps in the execution of controls.
Fine-Tune correlation rules
- Fine-Tune Correlation Rules as Necessary:
- Define data normalization and correlation rules to ensure that events from different sources are accurately analyzed.
- Create custom rules, alerts, and dashboards tailored to your organization’s needs.
Implement SIEM solution
- Implementation:
- Set up the solution by installing the required software or hardware and necessary agents or connectors.
- Configure the system to ensure seamless integration with existing security frameworks.
- Develop and implement security policies to govern the use of the SIEM system.
Ongoing management and maintenance
- Ongoing Management and Maintenance:
- Provide continuous training, documentation, and support to team members.
- Conduct regular reviews and audits of the SIEM system to assess its effectiveness, compliance, and alignment with the organization’s security and compliance needs.
- Ensure that the SIEM system remains perpetually efficient, responsive, and effective by leveraging cloud-based solutions and professional services.
Key takeaways
- SIEM is not an automatic solution; it requires thoughtful implementation and constant refinements to account for new risks and scenarios that arise.
- Enterprises and security teams should incorporate best practices to ensure that their SIEM is tailored to their needs and desired use cases.
- The most crucial best practices include identifying specific requirements, establishing a response team and a plan, conducting test runs on use cases, and fine-tuning correlation rules as necessary.
By following these best practices, organizations can maximize the effectiveness of their SIEM solutions and ensure a robust cybersecurity posture.
Advantages of SGBox’s SIEM for companies
SGBox’s SIEM can adapt to companies of various sizes and specific cybersecurity needs. The modular architecture of the SGBox platform allows the flexible and progressive development of defense activities.
Here are the main advantages of adopting SIEM:
- Constant Monitoring: IT infrastructure is continuously and real-time monitored to detect potential threats instantly.
- Flexibility and Scalability: SIEM is a modular solution that can be easily implemented with new features based on the company’s security needs.
- Detailed and Intuitive Reports: results are provided through intuitive dashboards and reports, facilitating the identification of weaknesses in the network.
- Threat Analysis and Tracking: through the correlation of security information, it’s possible to trace the origin of attacks and anticipate their negative effects.
- Simplified Security Activity Management: SIEM simplifies the management of security activities.
Discover the SGBox SIEM>>
FAQ
What is the difference between SIEM and other security solutions?
Unlike tools such as Endpoint Detection and Response (EDR) or firewalls, a SIEM provides a centralized view of threats by aggregating data from multiple sources, and offers advanced analytics capabilities to correlate events and respond to complex incidents.
How can I ensure compliance with the SIEM?
SIEM systems can help you generate compliance and regulatory reports, making it easier to comply with data protection and security regulations.
What are the main advantages of SIEM?
SIEM systems provide real-time threat detection, user activity monitoring, detailed reporting and overall security improvement for your business.




